Understanding Security By Obscurity Baeldung On Computer Science
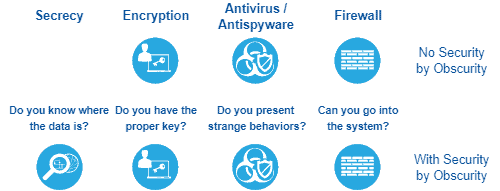
So basically we can define security by obscurity as the processes and methods to hide some data or. Security through obscurity STO is reliance upon secrecy in software development to minimize..
Security through obscurity or security by obscurity is the reliance on secrecy as the main method of providing security to a system or component specifically in security engineering whether on. Hiding security vulnerabilities in algorithms software andor hardware decreases the likelihood they will be repaired and increases the likelihood. So we in-depth explored security by obscurity presenting how it works inadequate use scenarios and good use scenarios We can conclude that security by obscurity is a powerful. It is commonly held that security through obscurity is only effective if used as one layer of security and not as the entire security system STO is a controversial topic in the IT. Security through obscurity or security by obscurity is the reliance on secrecy as the main method of providing security to a system or component specifically in security engineering whether on..
Exclusive Security Through Obscurity The Dangerous Approach That Work In Your Imaginationland Only Virusdie Blog
So we in-depth explored security by obscurity presenting how it works inadequate use scenarios and. The report considers the four major types of attacks Evasion poisoning privacy and abuse attacks..
Security through obscurity or security by obscurity is the reliance on secrecy as the main method of providing security to a system or component specifically in. Security by obscurity is in essence an insecure concept in that it means that the hidden secret or unknown entity is the key to unlocking the entire system In this case once the enemy. We can conclude that security by obscurity is a powerful security method if well used This method acts on reducing the probability of executing successful attacks on. This definition explains the STO approach to security which lies in protecting software secrecy There is a discussion of various approaches including security by. Security through obscurity STO is a process of implementing security within a system by enforcing secrecy and confidentiality of the systems internal design architecture..
Comments